Overview
This article explains how to verify your FTP or SSH connection to a DreamHost server is authentic and secured.
If you follow the steps in this article and the fingerprint values do not match what shows in your DreamHost panel, DO NOT CONNECT to the server. Contact DreamHost support so they may investigate why the fingerprints are different.
Background
Every DreamHost server has several unique SSH keys assigned to it. These keys are used to identify the server and ensure your connection is safe and trusted. When you first use an SSH program or terminal to connect to your server, it checks these keys.
If you have never connected to your server (or if the keys changed), you will see this warning:
The authenticity of host 'pdx1-shared-a3-05.dreamhost.com (69.163.140.5)' can't be established. ED25519 key fingerprint is SHA256:IuO3r8KWrx3xcCM3nVBWk2eNvbFIKI0exWIJrrtd76Y. This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])?
This article explains how to verify that the fingerprint displayed is correct so you can proceed to safely log into the server.
Verifying the fingerprint
There are two options to verify the fingerprint displayed in the warning message.
Option 1 — Use the panel
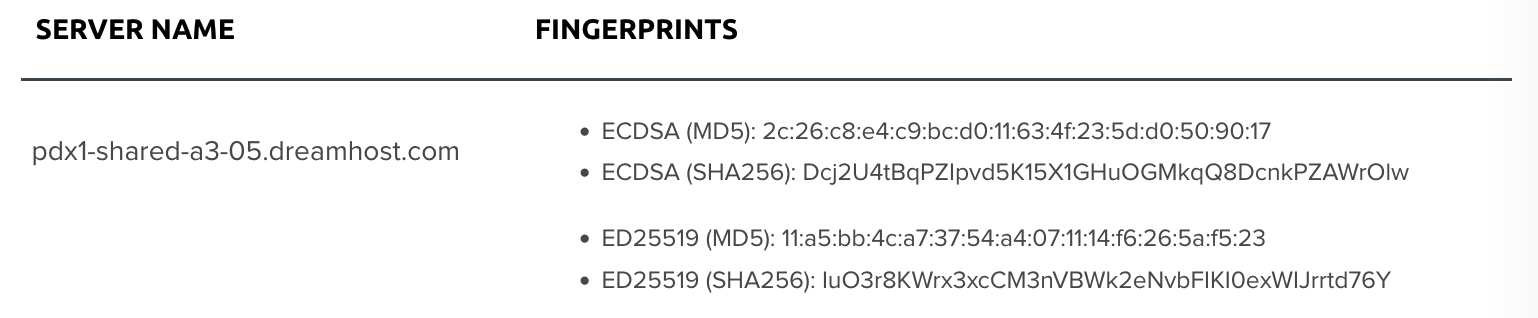
- Navigate to the SSH Keys page. Here you'll see your server along with its matching fingerprints.
- Compare the fingerprint in the warning message to the panel fingerprint to confirm it's the same server.
- Proceed as follows:
- If they do not match: Do not connect. Contact DreamHost support for further assistance.
- If they match: Accept the warning and connect to your server.
Option 2 — Use SSH
You can use SSH to verify the server's fingerprint with the FingerprintHash command.
These commands can be run on your local computer within your SSH client.
The examples below use the Shared Hosting server pdx1-shared-a3-05.
ECDSA
-
Check the ECDSA (MD5) fingerprint
[local]$ ssh -o HostKeyAlgorithms=ecdsa-sha2-nistp256 -o FingerprintHash=md5 pdx1-shared-a3-05.dreamhost.com The authenticity of host 'pdx1-shared-a3-05.dreamhost.com (69.163.140.5)' can't be established. ECDSA key fingerprint is MD5:2c:26:c8:e4:c9:bc:d0:11:63:4f:23:5d:d0:50:90:17.
Check the ECDSA (SHA256) fingerprint
[local]$ ssh -o HostKeyAlgorithms=ecdsa-sha2-nistp256 -o FingerprintHash=sha256 pdx1-shared-a3-05.dreamhost.com The authenticity of host 'pdx1-shared-a3-05.dreamhost.com (69.163.140.5)' can't be established.
ECDSA key fingerprint is SHA256:Dcj2U4tBqPZIpvd5K15X1GHuOGMkqQ8DcnkPZAWrOlw.
ED25519
-
Check the ED25519 (MD5) fingerprint
[local]$ ssh -o HostKeyAlgorithms=ssh-ed25519 -o FingerprintHash=md5 pdx1-shared-a3-05.dreamhost.com The authenticity of host 'pdx1-shared-a3-05.dreamhost.com (69.163.140.5)' can't be established. ED25519 key fingerprint is MD5:11:a5:bb:4c:a7:37:54:a4:07:11:14:f6:26:5a:f5:23.
Check the ED25519 (SH256) fingerprint
[local]$ ssh -o HostKeyAlgorithms=ssh-ed25519 -o FingerprintHash=sha256 pdx1-shared-a3-05.dreamhost.com The authenticity of host 'pdx1-shared-a3-05.dreamhost.com (69.163.140.5)' can't be established. ED25519 key fingerprint is SHA256:IuO3r8KWrx3xcCM3nVBWk2eNvbFIKI0exWIJrrtd76Y.